The SPIN software
Introduction
The SPIN software comprises several distinct parts:
- A traffic collector, to capture device traffic metadata and history
- A Visualizer, to show the traffic of the local devices
- A local publication system and JSON-RPC api, so other applications can perform further analysis and implement mitigation functionality
Features
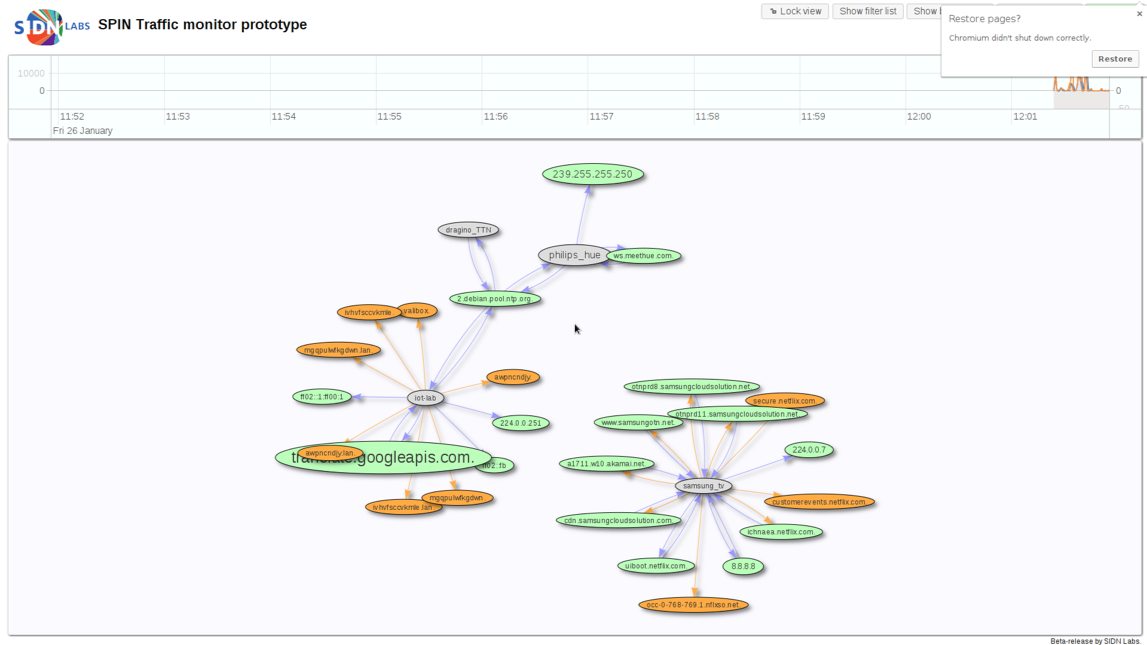
Visualization
SPIN visualises traffic flows so that the user can see what is happening on the network. From this interface, users can block traffic, as well as start a complete capture of the traffic of the network devices.
Reverse firewall potential
Through the visualisation interface, users can block traffic to and from specific endpoints or devices. This functionality can potentially be automated as well, as an early prototype of a reverse firewall on top of SPIN has shown; in this prototype, we kept track of the number of connections devices make, and if it suddenly exceeds a specific treshold, the device is quarantined. Smarter and more in-depth analysis techniques for mitigations such as this are a subject for ongoing and future research.
Anomaly detection
Anomaly detection by SPIN will look at creating machine learning models and time-series based analysis to classify devices and their traffic. This is currently in a very early stage. SPIN does have a small proof of concept, which simply averages the number of connections a device makes, and can quarantine the device if it exceeds a certain treshold.

Other usages
In addition to making SPIN available as a platform for in-home IoT security systems, SPIN is also used as a vehicle for security research, for instance by allowing users to collect, and optionally share, device traffic information and analyses.
Architecture
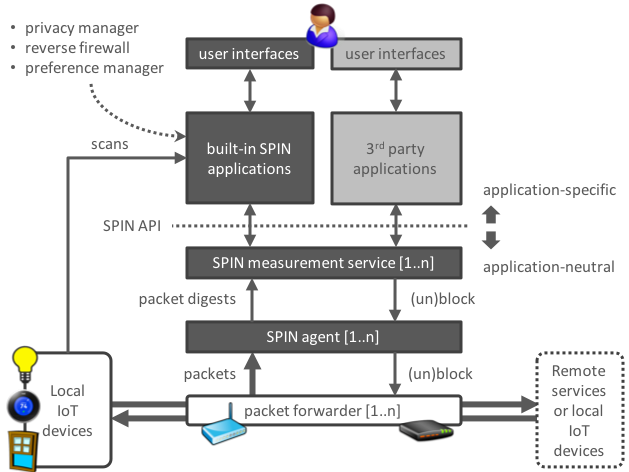
The figure above (click to enlarge) is a global overview of the architecture of a SPIN-based system, featuring two distinct component groups: lightweight SPIN agents that measure network traffic and more intelligent controllers. The separation is new and enables us to use the system for a larger set of deployment scenarios.
An agent captures traffic flows, generates flow digests, and can block traffic flows. A controller receives digests from one or more agents, analyses them, and can order the agents to block the traffic flows from certain IoT devices. For example, a controller may detect that a device is generating traffic flows that match the Mirai botnet. The controller then orders the appropriate agent to quarantine (block) the infected device.
Controllers and agents may be hosted on the same device, but our new design also supports deployment scenarios with several agents and one or a few controllers elsewhere in the network. For example, there may be a separate Wi-Fi hotspot on each floor of a house, each with its own agent and all governed by a central controller that runs on a general-purpose, always-on device such as a network-attached storage (NAS) device.
The SPIN platform can be extended with application components that can be implemented by (commercial) organisations, the SPIN community, or by the research community.
A well-defined API provides application developers with necessary of the home network and its IoT devices so developers don’t have to deal with the particularities of low-level measurements.
Download
SPIN comes pre-installed on Valibox router images, available for GL-Inet devices, Raspberry Pi 3, and as a VirtualBox image.
For other systems, such as Debian and Raspbian, you will need to compile it yourself for now, instructions for that can be found on the Github page.